Our unique managed SOC approach
Knowledge of the client’s risks, its technical environment and its organisation is essential for the SOC to be able to carry out all its activities. We carry out an initial assessment of your environment to understand your organisation, your technical context, your business and the associated risks.
This insight enables us to prioritise risk coverage with you and control the “Time-To-Detect” of the serious threats to your organisation.
Efficiency is maximised by the close proximity between the customer and Hashport. The customer has direct access to our analysts who will work hand in hand with the customer’s operational security and production teams, for which Hashport is a true extension.
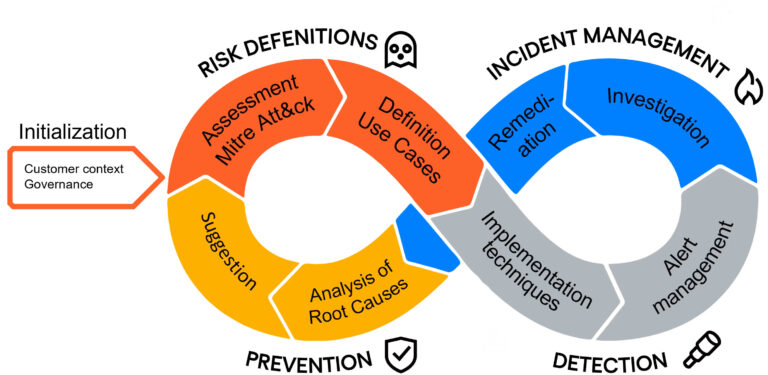
1. Initialisation phase
The initialisation of the service allows Nomios to get to know the technical, functional and organisational context. This discovery of your environment and your specificities is done through workshops covering your organisation and the personnel with whom the SOC will work.
This phase also allows us to frame the governance of the service with the final versions of the Service Agreement, Quality Assurance Plan and Security Assurance Plan.
2. Assessment phase
Cyber risk analysis based on the Mitre Att&ck model:
- External risk assessment, based on multiple cyber threat intelligence sources. Qualification of the real risks to the organisation.
- Internal defences: analysis of your internal security situation, including policy, security tools and organisational structure.
- Consolidation: the cross-referencing of all this data will make it possible to highlight the techniques most at risk for your organisation and thus define the priorities in the actions to be taken.
3. Detection phase
This step consists of the technical implementation of the use-cases in the existing security components: SIEM/XDR, EDR, NDR and SOAR.
4. Incident management phase
After enriching the alerts (investigation, sandboxes), the correlation of indicators and the history of alerts known by the SOC makes it possible to refine the criticality of the alert to qualify it as an incident.
5. Prevention phase
Monthly analysis and consolidation of incidents in order to highlight recurring incidents. The re-evaluation of Mitre Att&ck risks and the search for root-causes allow us to propose improvement plans at each iteration of the process.
